AXYS is deployed directly in your own cloud or on-premises environment, inheriting all your existing security controls, firewall rules, and compliance policies by default. The platform operates entirely within your private infrastructure, so your data never leaves your environment. AXYS works with your established security groups, identity management, and DevOps standards, ensuring seamless alignment with your organization’s best practices. All AXYS APIs are secured with robust authentication and tokenization, giving you full control over data access and permissions. For extra protection, AXYS can run entirely behind your firewall, maintaining strict privacy and regulatory compliance at all times.
Latest
From the blog
The latest industry news, interviews, technologies, and resources. View all postsTop 5 Checklist for Enterprise Search and Data Fabric Integration
In today’s fast-paced business environment, businesses need to be able to quickly and easily access essential data. One of the...
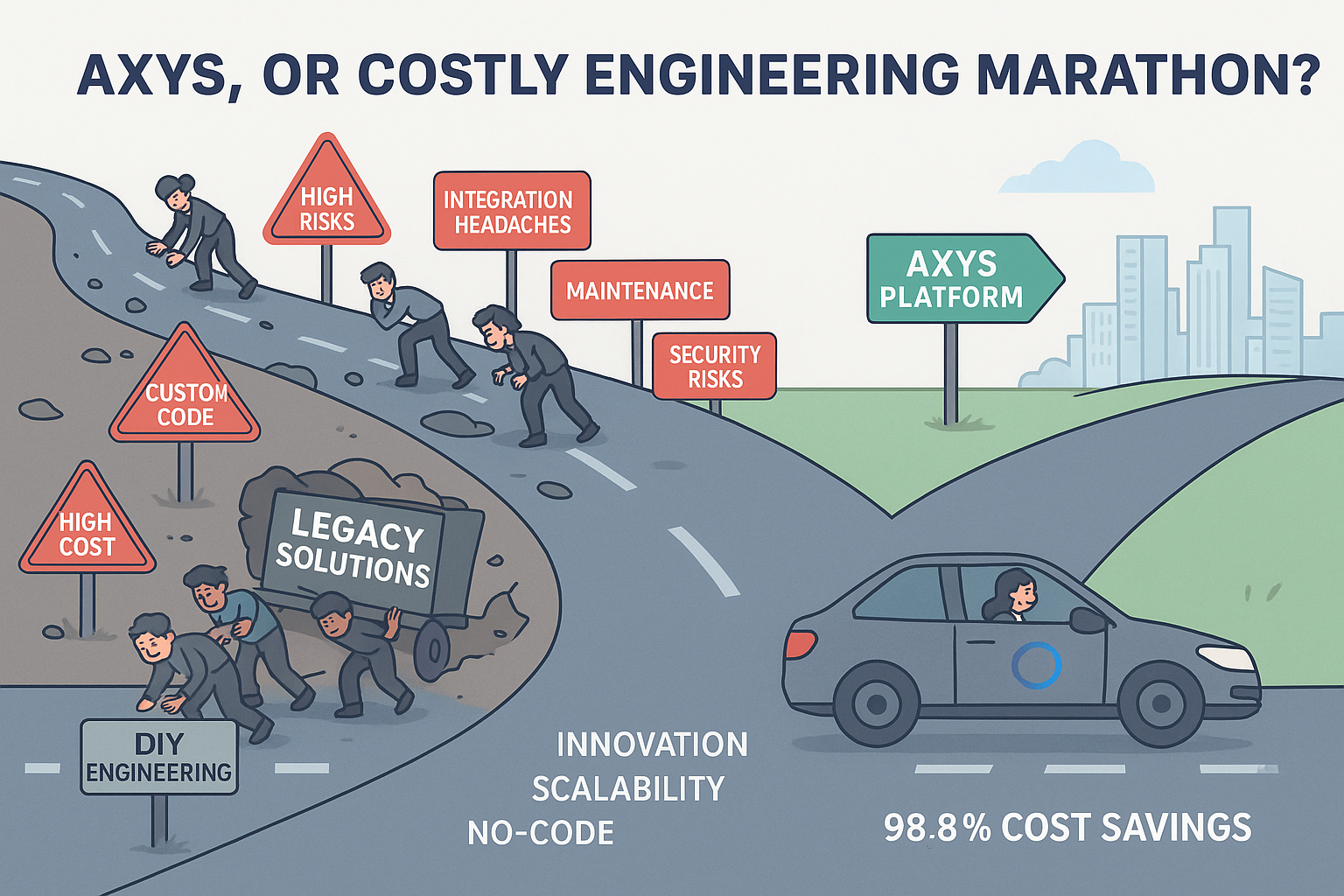
AXYS, Or Costly Engineering Marathon?
Why settle for complexity? There’s only one platform that unifies MCP, A2A, RAG, and more—with no code, no hassle, and...
Unlocking AI Agent Adoption: How AXYS Empowers Businesses to Scale AI with Confidence
AI Agent adoption in business has the potential to revolutionize everything from automation to real-time decision-making. But for most companies...
Still thinking about it?
By submitting this form, you agree to our privacy policy.